Authenticate 2023: Day 1 Recap

By: FIDO Staff
What is the current state of authentication? How is passkey adoption coming along across the globe? What are the big issues facing organizations for authentication? Those were among the many topics discussed on the first day of the Authenticate 2023 conference, which got underway at the Omni La Costa Resort in Carlsbad, California on Oct. 17.

The opening keynote for the event was delivered by FIDO Alliance Executive Director and CMO Andrew Shikiar, who provided a summary of the organization’s work over the past year to promote passwordless authentication using passkeys.
“The technology is ready, virtually every modern computing device can support passkeys,” he said. “That means that virtually every customer of yours, every employee of yours can use passkeys instead of passwords.”
Passkeys didn’t magically emerge overnight, rather there has been significant effort that has gone into the FIDO technical specifications over the years. In fact, Shikiar calculated that there has been over 60,000 hours of effort that have gone into FIDO technical specifications so far.
Looking ahead, Shikiar said that the FIDO Alliance has several key items on its to-do list for 2024, including consumer education, advancing adoption in regulated industries, encouraging an open ecosystem, helping developers to integrate the technology and regulatory engagement to make sure passkeys are part of updated guidance and regulations.
How AI Has Changed Hacking
The importance of strong authentication and passkeys was laid bare in an eye opening keynote by ethical hacker Rachel Tobac.

During her keynote, Tobac discussed how social engineering risks and AI is impacting hacking techniques. She detailed common attacks like phishing, tech support scams, and impersonation. She also demonstrated how attackers can use publicly available information and AI tools like voice cloning to impersonate people. In a somewhat tense moment, Tobac showed FIDO’s Shikiar how easily she could clone his voice and get him to say anything she wanted (she decided to get the AI cloned voice to say he likes cats).
Tobac suggests that users be politely paranoid overall and take steps to confirm that people are who they say they are. Among the best ways to improve authentication is the use of FIDO based strong authentication.
“Most everybody is reusing their password and most everyday folks are not using multi factor authentication at all,” she said. “Helping them move towards the right method of multi factor authentication for their threat model, especially if they have admin access, with something like FIDO is a really good move.”
FIDO helps orgs to save money too
As part of the morning keynotes, Derek Hanson, vice president of standards at Yubico, detailed different methods that organizations are using to reduce risk.

A primary way to reduce risk is by improvising identity authentication.
“We need phishing resistant authentication for everyone, everywhere,” he said. “FIDO lays the tools for a lot of those foundations for us.”
Hanson also detailed a brief case study of FIDO adoption by call center operations provider Afni. He noted that by supporting FIDO, Afni was able to substantially improve user experience and reduce risks, so much so that even the company’s cyber insurance provider took notice and lowered the company’s premiums.
Embracing the sound and the fury of the passwordless revolution at Microsoft
As part of the morning keynotes, Pamela Dingle, Director of Identity Standards at Microsoft, provided updates on the state of password attacks and how her company is working to strengthen authentication.
“Last year, I gave a number and this number was 1,000 password attacks a second, that is what we as Microsoft were seeing on our platform,” Dingle said. “Does anyone want to guess what that number is now? Well, that number is now 4,000 password attacks a second.”
Dingle highlighted how Microsoft has iterated on authentication methods based on real-world usage data to help improve security and reduce risk. She also outlined multiple efforts underway at Microsoft to improve user identity and authentication including token theft detection and privileged roles. She also showcased Microsoft’s implementation of passwordless authentication using passkeys on Windows 11. In her view, with the ability to sync passkeys across devices, the passkeys could eliminate the weaknesses of passwords if widely adopted.
Google, TikTok and eBay talk identity
Leaders from Google, eBay, and TikTok gathered for a live broadcast of the Identity at the Center podcast during the keynote to talk about innovations in digital identity.
Mahendar Madhavan, group product manager, eBay noted that his company was an early adopter of FIDO strong authentication and the WebAuthn specifications. While specifications matter he emphasized that user experience is critical.
“At eBay, users don’t see authentication as a thing that they need to do, they worry about buying and selling and the same applies to Google, they just want to search, at TikTok they want to make videos, right?”Madhavan said. “Authentication is the last thing that they worry about, right? So to be able to create smart contextual authentication that works seamlessly across devices is of paramount importance.”
Christiaan Brand, product manager of identity and security at Google, explained that his organization is increasingly nudging its users toward using passkeys as a default option for authentication.
“We want to gradually turn that volume upwards with the rest of the industry and that’s why it’s so important also to have my partners here with us on stage because I don’t think passkeys is something that one company alone can take forward and make a success,” Brand said.
Helping to secure and improve the user experience is also why TikTok is moving to adopt passkeys as well.
“The technology has obviously been adopted by a lot of big players in the industry and TikTok wants to be a part of that,” Daniel Grube, product manager at TikTok said.
The intersection of biometrics and authentication
Multiple speakers on Day 1 of Authenticate 2023 discussed the topics of biometrics, among them was Stephanie Schuckers, professor at Clarkson University and Director of the Biometric Institute.

“Biometrics is a key enabler for digital identity and remote identity verification systems, but there are also privacy concerns that individuals and organizations have,” Schuckers said.
Schuckers provided an overview of biometrics and guidelines for responsible adoption of biometrics technology according to the Biometrics Institute. She discussed how biometrics can enable digital identity but also raises privacy concerns. Shuckers emphasized following a process of first understanding the problem, legal framework, and risks before considering technology options.
Google gears up for #passkeysweek
In an afternoon session Google staffers, Kateryna Semenova, Developer Relations Engineer and Eiji Kitamura, Google Developer Advocate, discussed how Google is expanding passkey enablement.
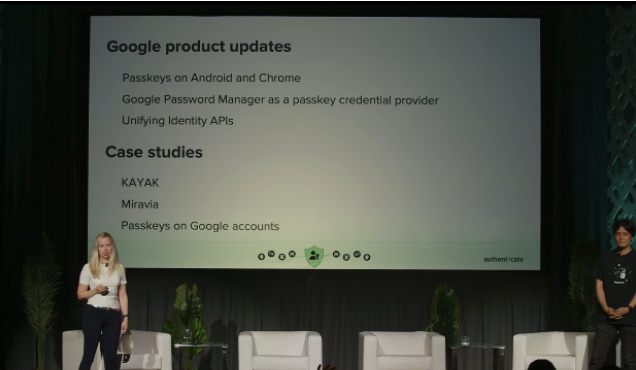
During the session, they detailed what’s new with passkeys on Android and Chrome, Google’s password managers and new unifying authentication APIs. They also shared case studies from partners who have implemented passkeys.
One of the big capabilities detailed by Semenova is for the Google Credential Manager which is a tool that can be used to consolidate different authentication methods, with the new default choice leaning towards passkeys. She also detailed how travel website Kayak has been able to transition to passkeys and in so doing has reduced sign-in time by as much as 50%.
To help push adoption of passkeys across Google and the industry, Kitamura announced that Google is advocating for a #passkeys week that will run from Oct. 23-27.
Cyber Hut: The numbers behind identity
In an afternoon session, Simon Moffat, the founder of the cyber security research firm The Cyber Hut provided some new insights about the state of identity and access management, based on his firm’s research.

When asked what identity components are likely to die off in the next year 30% of identity professional said password based authentication
“How do we kill the password? We have the technology, we have the standards and we have all of the wonderful ways of measuring benefits,” Moffatt said. “Yet, we’re all using passwords every single day.”
When asked what is stopping organizations from moving to passwordless, Moffat noted that the survey found that 64% of respondents said lack of coverage and integration was a barrier.
“It’s definitely a journey,” Moffat said. “I think organizations know passwords are bad and passwordless is great and what they struggle with is where to start.”
How Github’s Project Bulwark raised the bar on passwordless
Passkeys are being adopted quickly at one of the world’s most widely used developer sites.

GitHub staffers Hirsch Singhal, staff product manager and Hannah Gould, senior software engineer, discussed how passkeys helped the company successfully roll out mandatory two-factor authentication (2FA) for all users.
Singhal noted that GitHub has been committed to rolling out multi-factor authentication across its user base since at least 2022. He said that at the time two core issues with the technology was that it was hard to use and easy to lose. Passkeys help to solve those issues.
In the first three months of an open beta for passkeys, GitHub had 27,000 users. In only three weeks after GitHub made its passkey implementation generally available it got over 100,000 users. As to why the adoption was so rapid, Singhal said that GitHub followed FIDO Alliance guidelines for user interface design.
“We’re not even promoting passkeys or trying to push people to use passkeys,” he said. “I would attribute this mostly to the growth that the rest of the ecosystem has and also we were lucky enough to ship at the same time as both Google and Microsoft were making a lot of noise about passkeys working in their own ecosystem.”
Passkeys and regulated markets
Passkeys can also fit into regulated environments, according to Rolf Lindemann, vice president of products at Nok Nok.

In a session, Lindemann detailed how passkeys can improve security and usability for authentication, especially in regulated industries like banking. Lindemann discussed how passkeys address some limitations of traditional authentication methods and how they can help with multi-device usage. He noted that current regulatory requirements say regulated entities are responsible for handling device additions which could potentially be a challenge for synced passkeys. That said, Lindemann said there are solutions.
“Synced passkeys can be augmented to implement strong device binding, which is required for regulated entities,” he said.
Potential challenges to be aware of for passkey deployment
Passkeys offer tremendous potential for users and organizations, but there are some deployment issues that need to be considered regarding registration, authentication, and account recovery when implementing passwordless authentication.

Hans Reichenbach, Software Architect at Okta, noted that one of the pitfalls he has seen with passkeys has to do with domains. He explained that the way FIDO phishing resistance works is that it’s bound to the domain the credentials are registered on.
“So the domain you have at your registration needs to be the same domain as you have your authentication stuff, and you better like it, because if you change it, everybody’s gonna have to re-enroll,” he said.
Revocation is also different with passkeys then with passwords. Reichenbach said that revocation in the password world is an atomic action, where an administrator deletes one password and then can create another.
“That is not how it works with passkeys,” he said. “You need to register the new passkey first and then remove the old one, because otherwise you’re just totally locked out and have no credentials. “
The first day of Authenticate 2023 also had a bit of a somber note, as long time FIDO contributor Vittorio Bertocci who recently passed away was remembered and acknowledged with the launch of a new award in his honor, administered by the Digital Identity Advancement Foundation.
Day 2 of Authenticate 2023 is underway on Oct 17 and there’s lots more to come, with more user stories, panels and guidance. To register to join the conference in Carlsbad or attend remotely, visit authenticatecon.com.