Recap: Virtual Summit: Demystifying Passkey Implementations

By: FIDO staff
Passkeys hold the promise of enabling simpler, strong authentication. But first organizations, governments and individuals will have to adopt the technology – and some of them have questions.
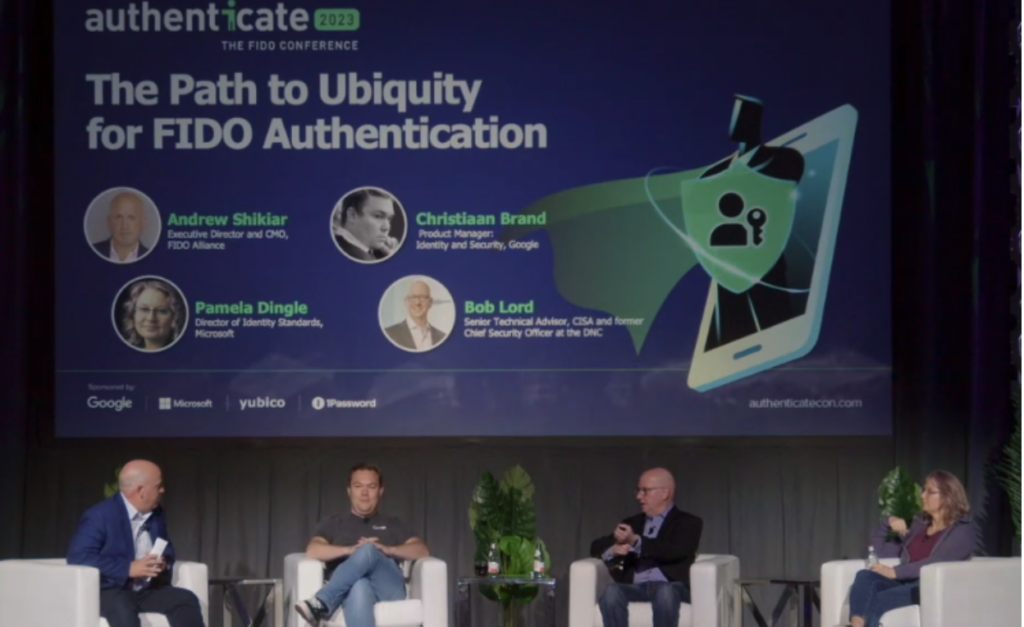
At the Authenticate Virtual Summit: Demystifying Passkey Implementation on March 13, speakers from the FIDO Alliance, Intercede, IDEMIA, Yubico, Dashlane and 1Password as well as implementers including Amazon and Target, presented on their experiences implementing and working with passkeys. The virtual summit covered the technical perspective on passkeys from the FIDO Alliance, as well as use cases for passkeys in the enterprise, consumer authentication, and the U.S. government. Along the way, attendees asked lots of questions and got lots of insightful answers.

Fundamentally a key theme that resonated throughout the virtual summit was that passkeys are a password replacement – and it’s a replacement that can’t come soon enough.
“Passwords are still the primary way for logging on and they are still easily phished through social engineering and they tend to be very difficult to use and to maintain,” David Turner, senior director of standards development at the FIDO Alliance said. “The consequences are real and the impact is real to the world at large.”
Passkeys 101
During his session, Turner provided a high-level overview on what passkeys are and how they work.
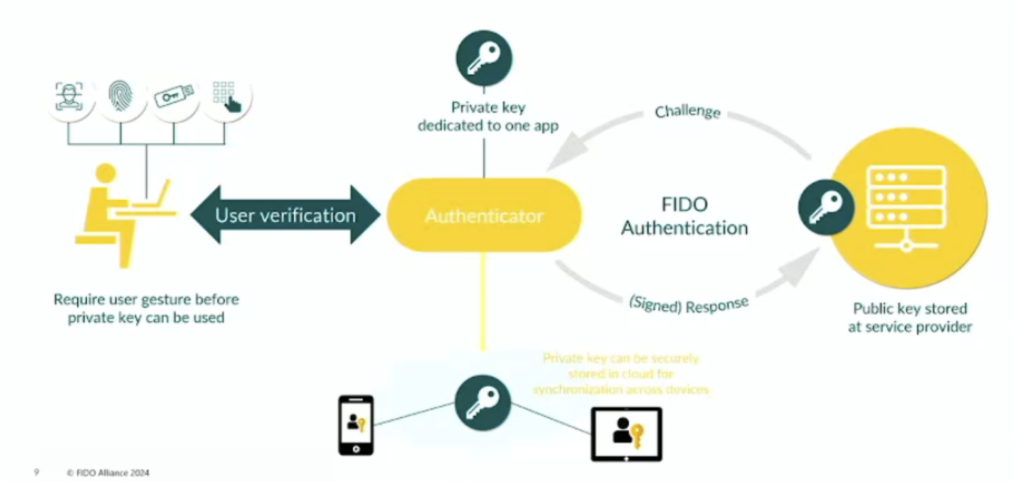
Passkeys build upon existing FIDO authentication protocols and simplify the user experience.
Passkeys can now be synchronized across devices through the use of passkey providers, removing the need for separate credentials on each device. Passkeys also enable new capabilities like cross-device authentication. Turner demonstrated how a QR code scanned on one device can securely connect to credentials stored on another nearby device.
In addition to synced passkeys there are also device-bound passkeys, that rely on technologies like a security key to provide the required credentials.
The State of Passkeys
The current and future state of passkey adoption was the topic tackled by
Andrew Shikiar, executive director and CEO of the FIDO Alliance.
There are now hundreds of services, including the major platform vendors Microsoft, Apple and Google, representing billions of users, that support passkeys at this point in 2024.

“If you are a service provider and you wish to deploy passkeys, you can do so with high confidence that your consumers will be able to leverage them,” he said.
The FIDO Alliance aims to drive passkey support over the coming years, in part by sharing best practices and success stories, which is a core part of what the virtual summit was all about.
Usability was emphasized as a key factor for widespread adoption.
“Usability is paramount. It must be front and center in what you do,” said Shikiar.
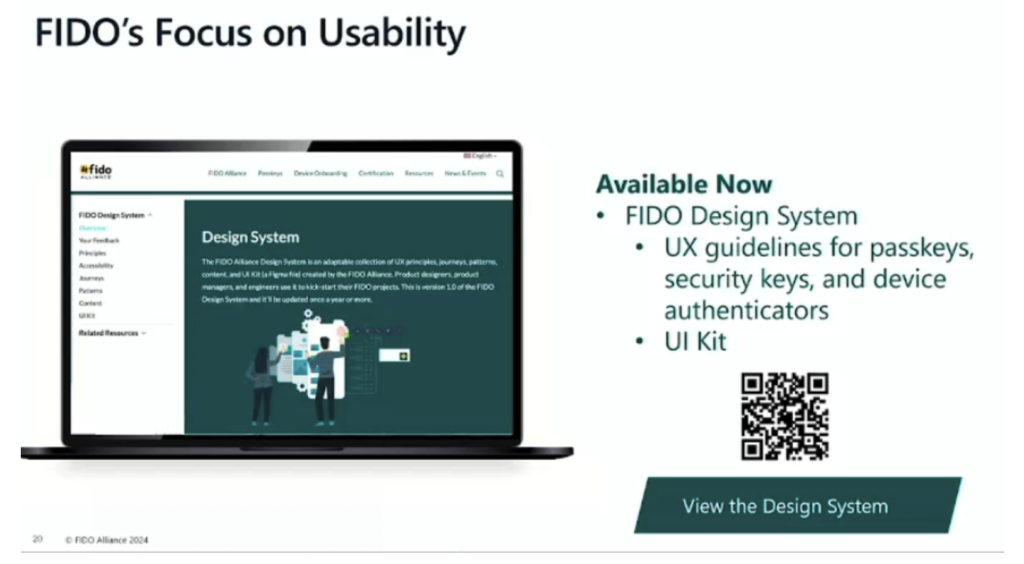
The FIDO Alliance has released user experience guidelines and a design system to help companies implement passkeys in a user-friendly way. Future guidelines will address additional use cases.
Shikiar emphasized that passkeys are not about being a new addition to improve the security of passwords. His expectation is that passkeys will be seen as a true password replacement rather than just an attempt at bolstering existing authentication methods. He emphasized that the fundamental problem is passwords, and the goal should be replacing them, not just adding extra security layers on top of passwords. Shikiar wants people to stop thinking about multi-factor authentication factors and instead think about enabling phishing resistant identities.
Passkeys are on Target at Target
Passkeys are already in use at retail giant Target, helping to improve security and optimize authentication for its employees.
Tom Sheffield, senior director cybersecurity at Target, said that the company has been leveraging FIDO for workforce authentication since 2018 and adopted it as a primary authenticator in 2021.

One of the ways that Target has been able to more easily enable passkey support across its platforms is via Single Sign On (SSO).
“We have a very robust SSO environment across our web application suite,” Sheffield said. “So for us, that made it very easy to integrate FIDO into the SSO platform, and then therefore every application behind SSO automatically got the benefit of it.”
In terms of how Target was able to get its users to adopt passkeys quickly, Sheffield said that the option was communicated to users in the login flow, rather than trying to explain to users what they should do in an email.
Overall, Sheffield emphasized that if an organization is using OTP (one time passwords) today for multi-factor authentication (MFA), any form of FIDO will provide significantly better user experience and security.
“There have not been many security programs that I’ve been part of in my 25-year career in this space that offer you security and user experience simultaneously,” he said. “So if you’re using anything other than FIDO you’ve got a great opportunity to up your game and provide a great experience for users which should make you a hero.”
Authenticating a Billion Customers with Passkeys at Amazon
Among the biggest consumer-facing websites that supports passkeys today is online giant Amazon.

Yash Patodia, senior manager of product management at Amazon, detailed how passkeys were rolled out to hundreds of millions of consumers worldwide. Patodia explained Amazon’s motivation noting that passwords are relatively easy for a bad actor to crack. He noted that passkeys help customers to authenticate more easily than other methods with a better user experience.
Amazon implemented passkeys using different APIs for web, iOS, and Android platforms. Now available across devices, Amazon’s goal is to drive awareness and increase passkey adoption among its customer base over the next year. In his view, passkeys are well suited for mass adoption and early indications from Amazon’s user base are very encouraging.
“If you’re a consumer facing company who has a big customer base, definitely explore this option,” he said.
Considerations for FIDO and Passkeys in the US Government
The U.S. Government is no stranger to the world of strong authentication, with many staffers already using PIV (Personal Identity Verification) smart card credentials.
Teresa Wu from IDEMIA and Joe Scalone from Yubico, who both serve on the FIDO Alliance’s Government Deployment Working Group (GDWG), provided an overview of how passkeys can complement PIV credentials and support a zero trust security model.
As government agencies work to implement phishing-resistant multi-factor authentication, passkeys are an option that could provide a more seamless user experience than one-time passwords or hardware tokens.
“We are not here to replace PIV, we are here to supplement and use FIDO where PIV is not covered,” said Wu.
One area they see opportunities for FIDO is for federal contractors and employees who are not eligible for a PIV card due to their job functions. Currently these individuals rely on passwords for system access.
State of Passkey Portability Set to Improve
A critical aspect of user experience is the ability to change passkey providers and move from one provider to another, if that’s what the user wants to do.
With existing password managers and legacy passwords, the process of moving credentials isn’t particularly efficient or secure, according to Rew Islam from Dashlane and Nick Steele from 1Password. It’s a situation that the Credential Provider Special Interest Group within the FIDO Alliance is looking to solve with a new standard for securely porting passwords between different password/passkey management applications.
The group is developing a new Credential Exchange Protocol that will use hybrid public key encryption to securely transfer credentials; the effort also includes the development of a standardized data format for credential information.
“By having the standard credential format, it will allow for interoperability of sharing credentials between two different providers in different organizations,” Steele said.
A proof of concept demo for the credential exchange is currently set for May, during the FIDO Member Plenary in Osaka, Japan. Islam noted that the effort represents a real triumph for the power of FIDO to bring different competitive vendors together for common purpose.
Common Questions about Passkeys
The virtual summit was concluded with an ‘Ask Me Anything’ (AMA) session where attendees asked their most pressing questions on passkeys.
Among the big questions asked:
How should organizations consider choosing synced passkeys or device-bound passkeys from a security and usability perspective?
Turner answered that the first thing to make really clear is that synced passkeys are probably the right answer for the majority of use cases. That said, he noted that FIDO recognizes that there are some areas where people have a much higher risk profile, and in those cases the device- bound passkeys can provide an extra level of trust.
Can passkeys play a role in transaction signing?
Pedro Martinez from Thales responded that yes, passkeys can be used to sign transactions. He explained that the beauty of the FIDO protocol is that it is based on the signature of a challenge. As such, it’s possible to adjust the challenge in order to contain data related to a transaction that needs to be digitally signed.
When will passkeys be the default mode of authentication?
Shikiar said that he doesn’t think that all passwords will go away, but he is hopeful for a passwordless future.
“Sophisticated risk engines and anomaly detectors don’t really think twice about accepting a password,” he said. “But as passkeys become more prevalent and become the default all of a sudden using a password will be anomalous in and of itself.and I think that’s when we’ll be in the fabulous future when using a password is rightfully seen as a high risk and anomalous action.”